How Much are Leaked Credentials Selling for on the Dark Web?
/In today's digital world, sensitive information exchanges hands more frequently than ever. Additionally, the way organizations store credentials is changing—as we embrace both local storage and cloud storage.
While database platforms like Amazon S3, Amazon Glacier, Azure Virtual Disks, and NetApp's Cloud Volumes ONTAP are inherently secure, they're not immune to breaches. Additionally, in-house databases are left vulnerable when engineers shun best practices.
Data leaks are more common than we think—and often go publicized. They expose login credentials of customers and employees to nefarious actors. Usernames and passwords are quite valuable to bad actors. What lies beyond that gateway is a treasure trove of personal information, proprietary data, and more.
How should companies counteract this threat? We'll assess the leaked-credentials landscape, and jump into some best practices.
The Leaked Credentials Market
Most us have been privy to some high-profile data leaks over the years. Breaches within LinkedIn, Equifax, and Yahoo have exposed logins and PII of over 3.3 billion users. These events highlight just how fragile backend infrastructure is. While we'd like to believe our best and brightest are working behind the scenes, the truth is that humans still make mistakes—either honestly, or negligently. Sometimes release schedules and budgets clash with security best practices.
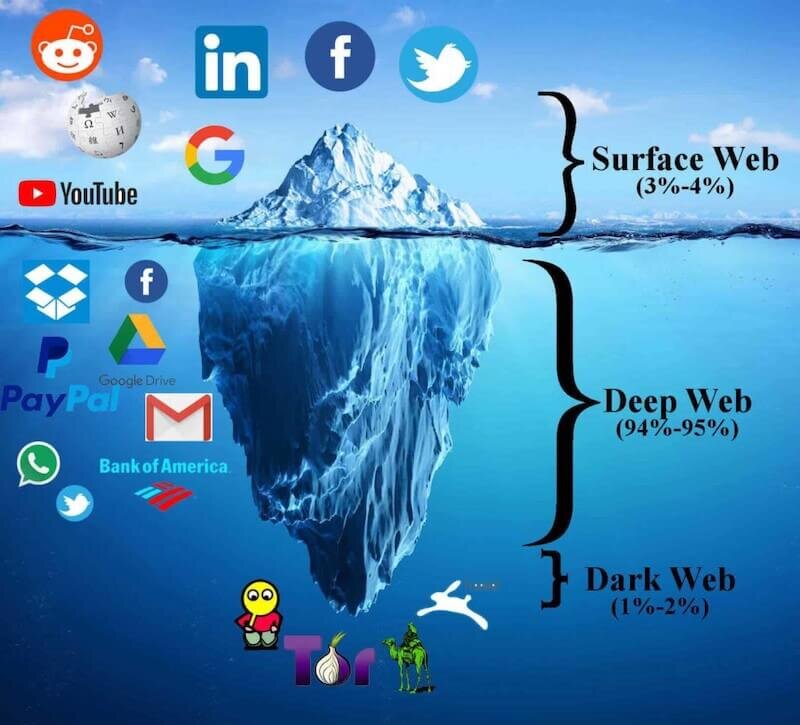
Don't forget: for each massive data breach, hundreds or even thousands take place simultaneously. While we don't hear about them, the collective impact is staggering. A 2020 report by Digital Shadows revealed that over 15 billion credentials are for sale on the dark web—a section of the internet not indexed by your everyday search engine, requiring special tools to access.
An Avenue for Profiteering
While the dark web remains a home for niche interests, it's become infamous due to rampant criminal activity. Many bad actors seek to profit from your credentials. Additionally, that information rarely falls into caring hands. What’s it selling for?
Sellers trade accounts for $15.43 on average, with bank accounts typically fetching $70.91
Domain admin accounts have sold for anywhere from $500 to $120,000 apiece (for an average of $3,139)
While most accounts offered these days are customer accounts, enterprise variants are many magnitudes more valuable. Misuse can cause massive disruption to services and corporate infrastructure.
It seems that brute force attacks aren't go anywhere. Digital Shadows CISO, Rick Holland, claims that many account checkers and cracking tools are selling for $4 on average. The barriers to entry for attackers are lower than ever. Hacking is now a white-collar crime with a blue collar price tag.
Given that the quantity of dark web credentials multiplied by over three times in two years, we can expect more credentials to become available daily. Companies have a responsibility to prevent such leaks.
Best Practices for Protecting Credentials
Organizations need to develop clear strategies for protecting their accounts. Those include testing and galvanization—to patch as many vulnerabilities as possible. It's impossible to make systems perfectly secure, yet careful companies shouldn't accept defeat. "How can we approach perfection" should be the question at hand. Here are some answers:
Vulnerability Defense and Testing
Credentials face threats at multiple points within an ecosystem. Passwords and usernames may be captured via malware, like key loggers. These malicious programs stealthily record everything you type, and route that information to a remote attacker.
While we might think an application should defend against this (which is possible using custom keyboards), the OS hosting an app or browser must play its part. Companies like Apple, Google, and Microsoft have a growing responsibility—even as our usage becomes increasingly mobile. Software patches can help prevent arbitrary code execution.
For example, mobile key logging vulnerabilities were most prevalent on Android phones and Apple devices that were jailbroken. These jailbroken devices are used to download unofficial software, and run outdated versions of iOS. However, cybersecurity company FireEye had found weaknesses on newer devices—or those wired to PCs.
Intelligently Integrate Your APIs
Credentials might also be captured after clicking "Sign In." A typical application uses APIs to connect users with data or functionality. These APIs essentially allow two pieces of software to communicate back and forth—transmitting data over the web each time.
It's possible to intercept this data. Companies therefore must vet the external APIs they use, and certainly the ones they create, before launching a service. That includes understanding which protocols to use (REST, SOAP, WebSockets) and how they're encrypted. A poorly-coded API is more sensitive to attack.
Test Early and Often
While many companies test after a service is in production, it's much more beneficial to test earlier on. Called shift-left testing, this strategy relies on finding as many bugs (and security holes) as possible before users are impacted.
Envision application development on a timeline. There are traditionally four basic stages in order of execution: design, develop, test, and release. Newer approaches are moving that testing phase backwards. It's also proven that early testing can help prevent breaches—as it provides a closer look at underlying infrastructure.
There's a financial incentive, too. Bugs caught earlier are less costly. Remediation doesn't require downtime, there's less (if any) public fallout, and the application is less complex than it would be later on. That means sifting through less code—and fewer breaking changes.
Ditch Plain Text for Hashing (with a Little Spice)
Never, ever store your passwords as plain text within your databases. This information is easily readable, should it fall into the wrong hands. It becomes doubly useful if exposed passwords are paired with usernames in tables. Cybercriminals must exert very little effort when putting those puzzle pieces together.
Instead, all organizations should rely on hashing, at minimum. This practice involves scrambling credentials into a randomized string of numbers and letters. To an attacker, these random values have little meaning. Hashing is also considered a one-way process. While it's easy to algorithmically hash a password, decoding that hash into plain text is nearly impossible.
Not all hashes differ. Engineers can thus employ two additional practices, called salting and peppering. Salting involves inserting random data into a hash function—making it form a password hash that's guaranteed to be unique. This is especially helpful if two users share the same password (more on that later).
Peppering tacks a value onto the end of a password before it's hashed—again producing a unique result. It's important to safeguard this secret value. Pepper characters should be generated randomly yet never stored. This means much more experimentation on the hacker's part.
These methods protect databases from three attack types:
Rainbow tables — Massive collections of organized, pre-collected hashes alongside hashing algorithms. Algorithms themselves are well-known, so testing them against stolen passwords and hashes is a rapid process
Dictionaries — Large collections of compromised pass-phrases, compared against stolen hashes, to uncover password matches
Brute force — An attacker rapidly submits passwords, one after the other, until they guess correctly
Hashing and salting don't just obfuscate your passwords. They add valuable time to the guessing game, which gives companies time to squash active attacks or lock hackers out.
Enforce Strong Password Policies
If tools like Active Directory have taught us anything, it's that password policies are exceptional security blankets. IT professionals can impart a number of guidelines for their users—both internal and external—when making passwords. These may include:
Forcing users to use special characters and combinations when setting a password
Forcing users to set a password of a specific (minimum) length
Forcing users to change their passwords periodically
Building ecosystem complexity makes it that much harder for bad actors to gain ground. Each login device is considered an endpoint—or critical access points that remote attackers can exploit under the right conditions. It's important to secure these endpoints, and certainly so when accounts are tied to certain devices or services. Strong passwords are low-hanging fruit in that regard.
Password policies can also enforce lockout after a number of failed attempts. This can prevent brute force success—yet must be smartly implemented, to avoid divorcing actual users from important account data. Extended lockouts can be frustrating.
Even at the administrative level, it's crucial that accounts with high-level privileges are protected. Passwords should contain more characters and be held to higher security standards. Since these users can access databases (containing credentials), we want to prevent impersonation or cracking.
Nailing the Fundamentals is Essential
You'd be surprised how many companies don't properly protect their sensitive data. Thankfully, you don't have to be one of them. By harnessing these tips, you'll save yourself plenty of future headache and avoid costly data breaches.
Need some help guarding your credentials against hackers? The Specops Password Auditor can help uncover leaked passwords in your environment—leading to quick changes, and stopping attackers before they act.